Before we start, we need to understand how carrier actually identifies your traffic from tethering. If you google, a lot of people will say carriers use TTL to detect tethering. While this could be true, it doesn’t seem like modifying TTL helps.
It’s actually pretty simple – the phone told the carrier on its own!
How do you know? Just go to whatsmyip.org and check if you IP addresses are the same from the phone and from a device that’s using the hotspot.
You will see that you actually get two different IPs! This means that as you’re tethering, the traffic isn’t sent through the same channel as the traffic on the phone!
As a matter of fact, when you’re tethering, the phone will use a different APN (usually called dun) instead of the regular APN that traffic goes through. It’s super easy for the carrier to then throttle your traffic.
Now we figured out that how carrier detects tethering traffic, let’s figure out how to bypass it.
Option 1: Use a device that doesn’t expose your traffic.
If you have a rooted Android phone, I believe you will be able to modify the iptable to route traffic to the phones “regular” apn. You might be able to find some MIFIs that will do this for you automatically on the market.
However, most of us no longer use rooted phones anymore, and this is basically impossible for iOS either. What do we do?
Option 2: Reroute traffic back to the “regular” link using a proxy.
There is a very interesting app called Every Proxy, which is able to setup a proxy server on the phone. If you point your other device (like a PC/mac) that connects to the hotspot to use the proxy, you will be able to reroute all the tethering traffic back to the phone – which the carrier will no longer be able to identify. For the proxy setup on the PC/mac, just use the system proxy settings for it
Now let’s see what I get:
Before:
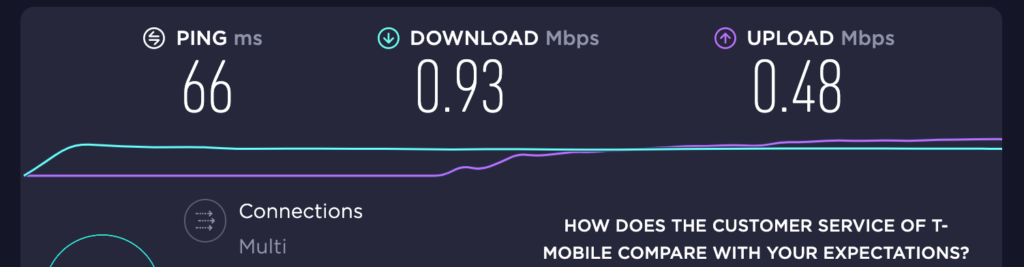
After
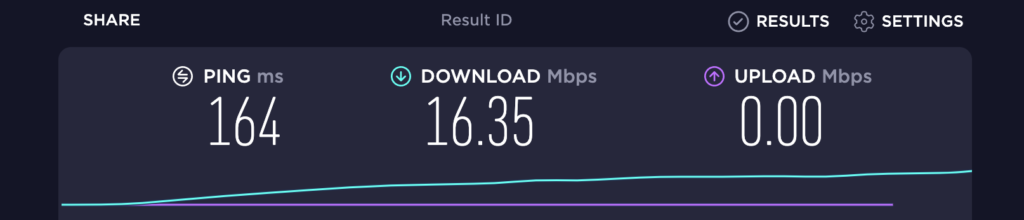
A significant improve I’d have to say!